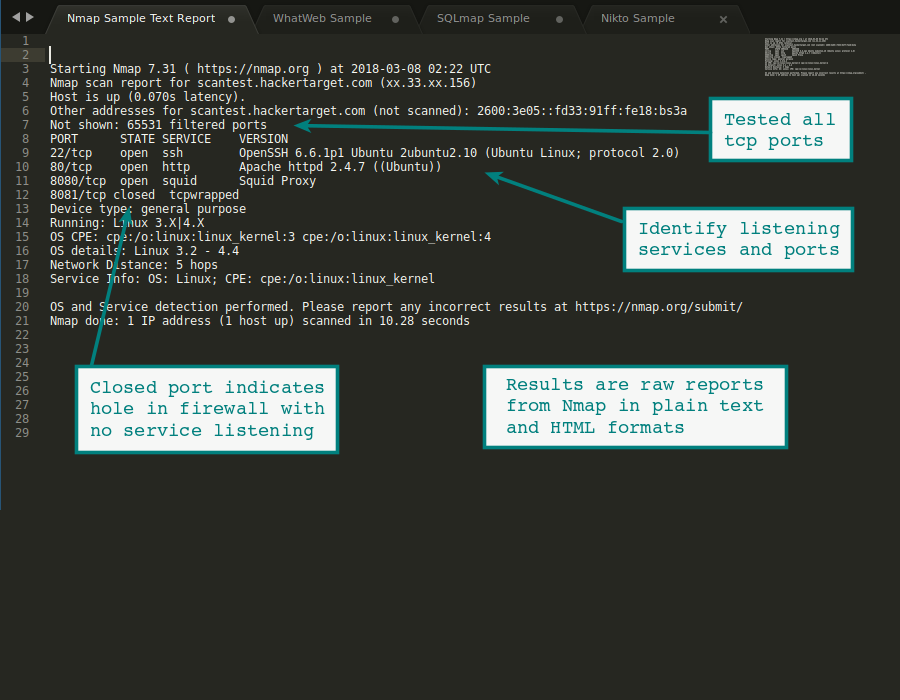
Method 2: nmap. Our prefered method. First make sure nmap is installed, if it isn’t run apt-get install nmap.Once installed you can use commands to check the SSL / TLS version using the ssl-enum-ciphers script. This script will let you scan a target and list all SSL protocols and ciphers that are available on that server.
Download:- Vidmate For PC, Windows 10 8 7 XP. Vidmate For PC Windows (8/8.1/10/7/XP/Vista), Laptop, Computer, Desktop 32, 64-bit Free Download. May 17, 2019 - Download Vidmate 2019 for PC free download latest version. License; Free; OS; Windows 10/7/XP; Language; English; Latest Release; 18 Sep 2018; Version; 3.38; File Size. Also available on Google Play store for Android. Windows 7 Professional Full Version Free Download ISO 32-64Bit 2019. With the help of this guide, Install VidMate for Windows 10, 7, 8. Two downsides of VidMate, One it has no PC version and it is not available on Google Play. Windows 7 64-bit free download. Feb 13, 2019 - You can free download Vidmate for PC software, Windows 10, 8.1, 8, 7. Windows 10, Windows 7, Windows 8, Windows 8.1 32 & 64 bit. In Bluestacks, you can install Vidmate app in 2 ways, one is using a Google play store.
Tls Version 1.2
- I am looking to see how to check the current TLS version on a linux box. We are needing to do some upgrades for payment requirements and need to check this out. In my research I found that there is no cmd that will spit out this info. Any help is greatly appreciated.
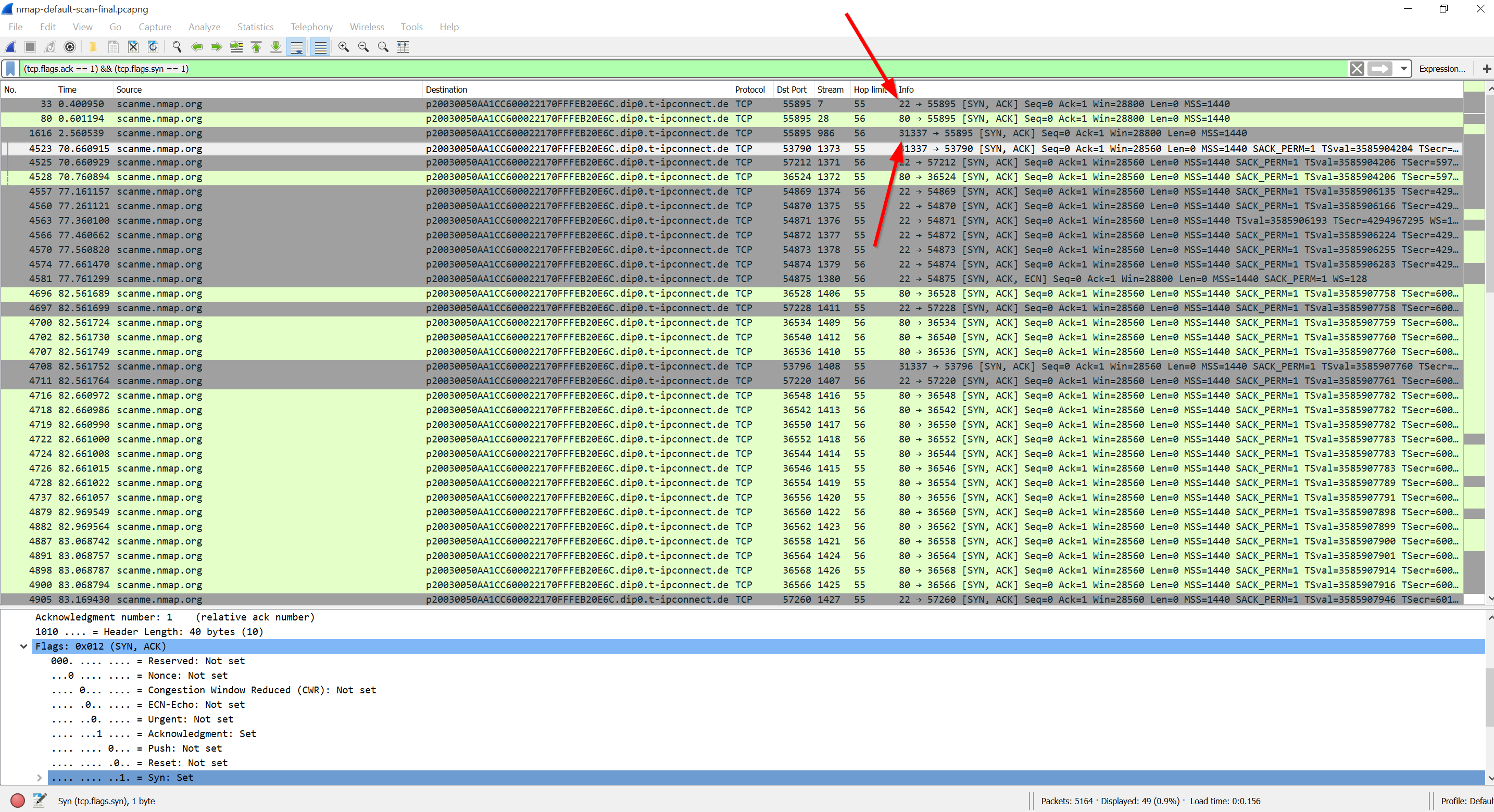
- Jump to Verify the agents using nmap - Nmap scan report for (X.X.X.X). If you still need to enable TLS 1.2 strong cipher suites,.
As far as I know Nmap is the oldest living port scanner, initially developed by Fyodor Vaskovich in 1997 to discover services and map networks, written initially in C was rewritten to C and highly improved by the Open Source community in its second release of 1998, it continues adding features and improvements until today.Nmap is another example about the altruist community’s power leading the technological development. Today the variety of configurations or parameters we can apply to a scan allows us to directly detect vulnerabilities, while years ago by using Nmap we could only suppose and test.
Tls Version Check
Currently the accuracy is a lot higher and we even can scan vulnerabilities with Nmap.Nmap works by delivering packets to the target and analyzing its responses but before continuing to talk about Nmap let’s remind some basics about networking including the most popular protocols, ICMP, TCP and UDP.Internet Control Message Protocol (ICMP)It is a protocol mainly used to send information rather than transporting data. Usually used to report errors when a request is done, that’s why, just like TCP or UDP, ICMP must not be underestimated. Examples of ICMP are the famous PING which returns information about the destination IP or the TRACEROUTE command under Windows (Under Linux the “traceroute” command by default uses UDP). Of course, we can give additional uses to this protocol, if my memory does not fail, forcing ICMP connection was one of the ways to bypass routers web based security login.Internet protocol suite (Known as TCP/IP)This is the most popular protocol, or suite of protocols. Initially one protocol later divided into two: TCP and IP. Starting Nmap 7.60 ( ) at 2017-12-17 09:57 ISTNSE: Loaded 101 scripts for scanning.NSE: Script Pre-scanning.Initiating NSE at 09:57Completed NSE at 09:58, 10.00s elapsedInitiating NSE at 09:58Completed NSE at 09:58, 0.00s elapsedInitiating Ping Scan at 09:58Scanning www.hiddendomainname.info (X.X.X.X (Target IP)) 4 portsCompleted Ping Scan at 09:58, 0.19s elapsed (1 total hosts)Initiating Parallel DNS resolution of 1 host. At 09:58Completed Parallel DNS resolution of 1 host.
Nmap Openssl Version
THIS IS WRONG. The second column in ciphers -v is the minimum version for the ciphersuite; since TLSv1.0 and 1.1 don't add any ciphersuites not present in SSLv3, in 1.0.1 and 1.0.2 this lists only SSLv3 and TLSv1.2 even though 1.0 and 1.1 are supported. In 1.1.0 due to an obvious bug 1.0 is listed, but 1.1 still is not. Also, 1.0.0-2 do support SSLv2 but don't put v2 suites in the default cipherstring, so it isn't listed; that could be fixed by using ALL. (OTOH both SSLv3 and SSLv3 are broken and should not be used.)–May 1 '18 at 5:23.